In the second half of 2015, we launched our IPS/IDS (Intrusion Prevention Systems and Intrusion Detection Systems). At first it was only tasked with monitoring traffic on our servers (it was an IDS). We were surprised by the huge number of attacks. For example, the number of attacks on the WordPress login page (wp-login.php) averaged 8 per second. Early last week (15.4.2019) we compared it and it was already a whopping 63 attempts per second. And we can only detect activity on HTTP so far. However, more than half of our services already use HTTPS.
The wp-login.php page has become the most visited page on all our sites. unbelievable…
The attacks and activity of useless bots have reached such a point that some servers have begun to experience intermittent slowdowns in customer service. The problem is that most of these attacks are only marginally detected because they are directed at sites using HTTPS.
For these sites we cannot use our IPS/IDS protection for the time being, because we cannot see the traffic. Our developers are currently working on a method to do this. But it is difficult, expensive and very error-prone, so deployment will take some time.
In addition, this will only work for the new NoLimit on HPE Moonshot (set up from November 2017), where proxy technology is used. But don’t worry, once everything is ironed out, we’ll be migrating. All of our customers will be migrated to HPE Moonshot, which use faster servers with 3.4 Ghz processors, NVMe SSDs and support for many new advanced technologies. Our NoLimit is evolving and we are just at the beginning of an amazing journey of technological advancement 😉
For now, DDoS protection and WEDOS honeypot will protect us
Our DDoS protection is composed of several layers. Part of it is in charge of brute force attacks and part of it deals with, let’s say, the smarter attacks. This year, coincidentally, we had the opportunity to test our defenses against some very sophisticated attacks. One was even quite successful. We had to add another layer just for that.
This layer also includes very fast filtering by attack origin and under quite specific conditions. Coincidentally, that’s what we’re going to need right now.
Since last year, we have been testing software to analyse large amounts of data. From all web hosts (about 103,000 active ones) absolutely all conceivable logs are downloaded to one central server. Here they are analysed, evaluated and displayed. All in real time. Currently, an average of 6 to 10 thousand records per second are logged.
It is from these logs that we get the basis for filtering. Simply put, if someone starts “banging” wp-login.php very quickly, even across servers, their IP address is quickly sent and blocked. So we actually made a big honeypot out of all the web hosts 🙂
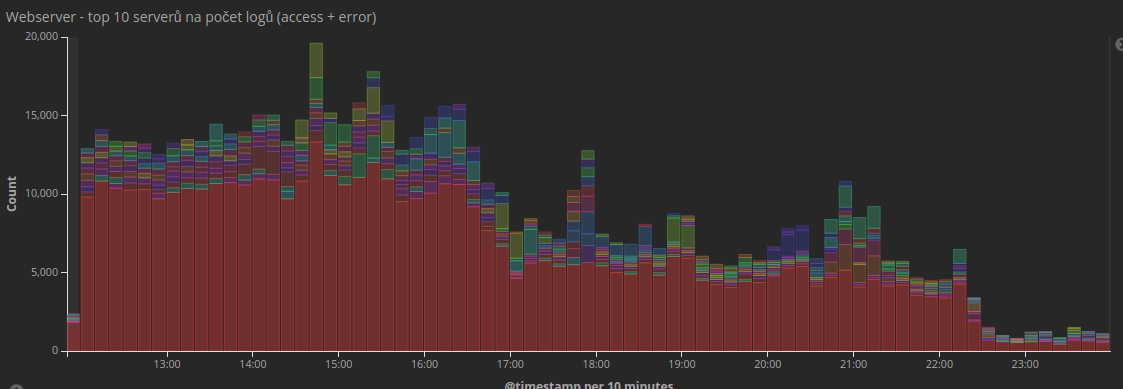
And this is what it looked like for the top 10 busiest servers:
As more attackers were added to the blacklist, the load on the servers decreased. Your sites will be much faster now thanks to the new protection, because most servers got bored again and that’s the way it should be 🙂
By the way, the big red column is the proxy servers that handled most of the traffic. If you have a good caching setup, they can make your site very fast because they take care of all the static content.
What we filter and how
At the moment, mainly bulk attacks on WordPress are filtered both via HTTP and HTTPS. We mainly focus on those that attack wp-login.php and xmlrpc.php. More will be added in the future.
We have also decided to be stricter with robots that are inconsiderate. They are mostly robots that collect data, or rather one could say spy on it, and use it for marketing purposes or offer data for SEO. One such robot even made 7% of all accesses to all websites hosted by us.
IP address filtering is set to 2 – 6 hours for now.
New filtration systems block an average of 45% of traffic! Further traffic is blocked by the IDS/ISP, which acts as an additional layer of filtering.
Can you help us make web hosting faster and more secure?
From our point of view, everything works faster and better. We have had no negative reactions since deployment. But that doesn’t mean we could have missed something. We would be grateful for your feedback on:
- Do you use an extended content management system or e-shop and regularly encounter attacks on a specific file?
- Is there a particular robot overloading your website that nobody needs?
- Soon we will offer to all services (including VPS and dedicated servers) the option of filtering by country (either you blacklist or whitelist some countries – we have tested and it works).
Conclusion
Thanks to the increased number of attacks and robot activity, the entire internet is slowing down in general. It’s not just our impression and it ‘s not just happening here. We are only more concerned because we host most small and medium-sized websites, which most often choose the WordPress content management system. It’s great and works well for us. Jen is number one for automated mass attacks. These usually fail, but still generate load.
We’ll bring you some statistics as we go along.
We therefore recommend that you use a security plugin such as WordFence.