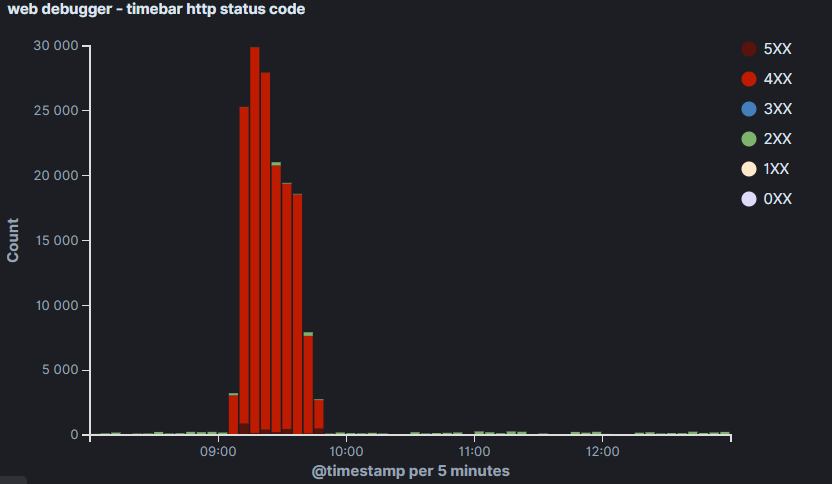
Last month, we showed you in the article “DDoS extortion cases on the application layer are starting to appear ” how the extortion and subsequent DDoS attack on a customer’s website takes place. We know that these cases are gradually increasing, but the pace is accelerating unpleasantly. In addition, we can see from the analysis of logs that attackers are trying to mask their attacks better, trying new methods and looking for the limits of protection.
Continue reading “Two more examples of application layer attacks on our customers”Cases of application layer DDoS extortion are beginning to emerge
Extortion by DDoS attack is nothing new. Large botnets can carry out a fairly powerful attack nowadays, which can easily clog several 100 Gbps routes(we have already seen this happen). Fortunately, they are relatively rare because they are expensive. Medium attacks (above 10 Gbps) are encountered more frequently (even several times a month). And smaller ones (under 10 Gbps) are almost a daily occurrence. However, this classical kind of brute force attack (in terms of data volume or packet count) is relatively well detected and filtered. It is worse with application layer attacks, such as those that try to pass themselves off as normal traffic.
Continue reading “Cases of application layer DDoS extortion are beginning to emerge”A wave of new and insidious attacks is coming and WEDOS is ready for it
We’ve written a lot about our protections. We wouldn’t be here without them. We are constantly improving them and trying to stay one step ahead. However, the progress we made last year was really significant and, as it turned out at the end of the year, very important.
Continue reading “A wave of new and insidious attacks is coming and WEDOS is ready for it”